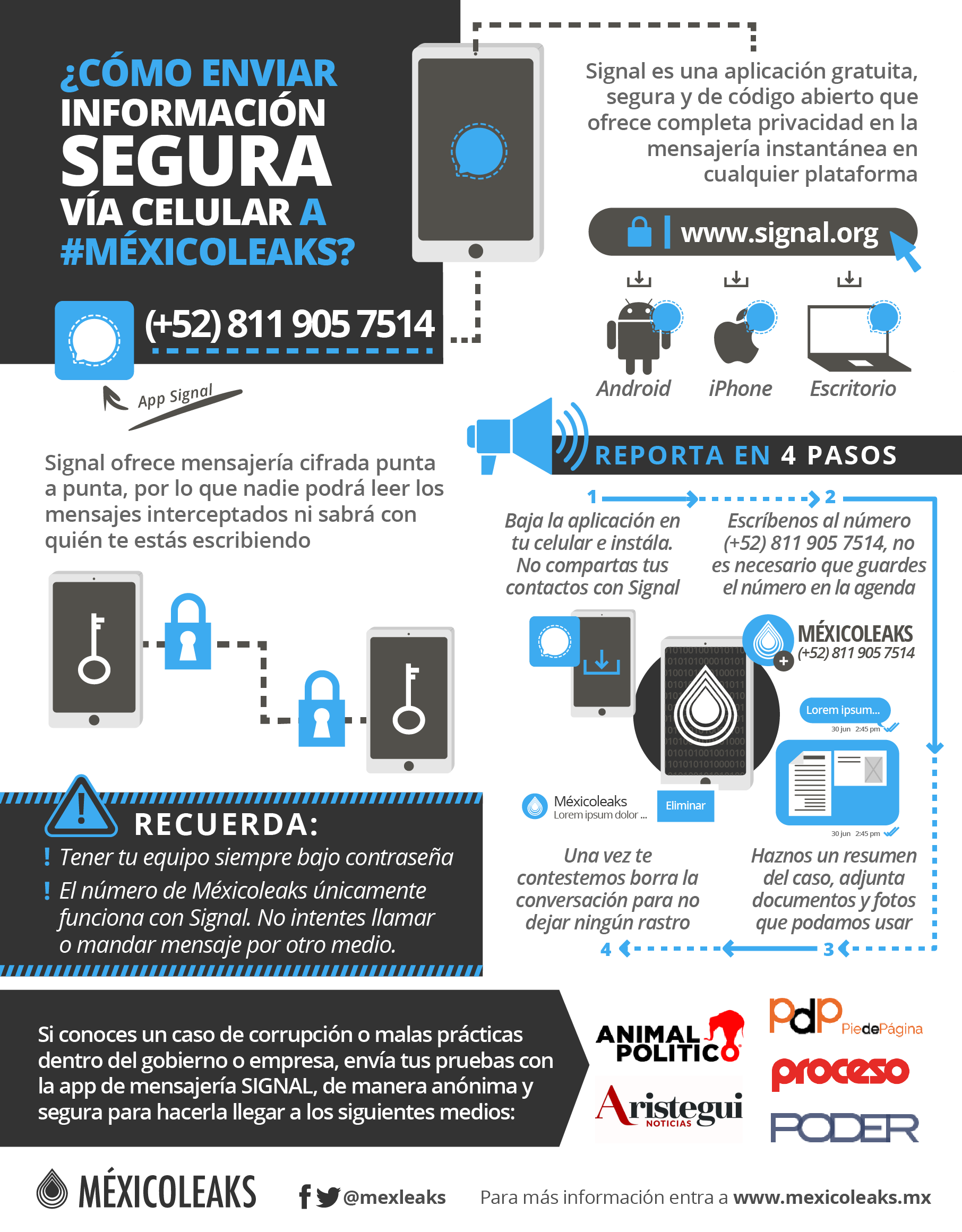
To access our secure and anonymous dropbox you must use the Tor Browser to hide your identity. Once downloaded and installed, use it to access mexicoleaks.mx and click on the 'Send documents' button.
Download Tor BrowserTor is a piece of software designed to allow you to browse the internet without revealing your IP address, through encrypted channels and no external leaks, allowing you to hide your identity. The program is ready to use and is designed for beginners and experts.
1. Tor helps you to hide your identity while using the internet, but if you reveal personal information while using Tor you can be identified even if your IP address (your identity on the internet) is hidden.
2. Tor is safe tool if used correctly. However, it is not perfect. To avoid problems it is important to update the browser when it asks you to, even more so if you want to access email accounts used to send sensitive information or any dropbox. The update will be announced in the browser once open, informing you if your version is obsolete.
If you want more information on the Tor Browser read this article on Wikipedia.
This whistleblowing submission platform is implemented using the GlobaLeaks software. Anonymity for the whistleblower is provided thanks to Tor Browser. The Browser is laready integrated.
Whistleblowing platform designed by the Hermes Center for Transparency and Digital Human Rights. Our code can be inspected by anybody to prove that it does what we say it does. For this, experts in security from around the world have done multple audits to identify and fix potential issues. This is the best way to assure that the tool is secure.
This is the best way to ensure that the application is truly secure. We do not ask you to blindly trust our security decisions: we have received various independent security analyses from third parties.
We understand that complete security cannot be guaranteed; however, we have designed this technology taking into account scenarios where a whistleblower’s life is at stake.
For more in-depth analysis of the security of GlobaLeaks, see: GlobaLeaks Application Security Design and Details.
When submitting sensitive information, you must consider the risks related to doing so, as you may be subjected to retaliation by parties that don’t like what you have to say.
This is why you must take all possible actions to preserve your anonymity.
To do this correctly, you need to be aware of the social and technical risks, in order to take the right countermeasures to protect yourself. Remember that finding the best protection strategies depends on the scenario, especially those related to social risks.
The aim of this guide is not to scare you, but to make you aware about the possible risks related to leaking confidential information. When exposing corruption and abuse, you are doing the right thing, however, you could suffer from retaliation by others involved. By understanding the risks you can take effective and precise actions to protect yourself. If this is done correctly, then you can protect your identity and avoid any problems. Before sending information, consider the following points:
Do you have a strong political or activist background?
Are you a public figure?
Do you have reasons to believe that you are being personally and/or physically surveilled?
Do you have reasons to believe that your computer may be compromised?
Please remember that these risks are potential risks. Being aware of them only increases your security. Take them into account and evaluate which security measures you should take to protect yourself.
Suggested: If you replied “yes” to one of the questions above, when submitting leaked confidential information consider using a computer which is not yours and a network connection which you do not normally use.
In the following sections we will detail the social and technological risks involved, as well as the solutions to avoid having to face them.
Considering what was mentioned above, from a social protection perspective you should consider taking the following set of actions:
Before you make a submission, don’t tell your intention to anyone;
After you make a submission, don’t tell what you have done to anyone;
After the news about the submission gets out to public media, just behave like any other clueless person;
Be aware of surveillance systems (cameras or other) in the place where you acquire and submit the information;
If you use a public internet connection to submit confidential information, don’t use your credit or debit card in the establishment; pay with cash;
Don’t look around on search engines or websites for the information you submitted (this would reveal that you knew about it earlier).
You must be aware of the fact that while using a computer and the internet to exchange information, most of your actions leave traces (computer logs) that could lead an investigator to identify where and who you are.
For this reason you must consider risk mitigation strategies and adopt very specific precautions to avoid leaving technological traces about what you are doing.
Remember that you may leave tracks while:
Researching the information to be submitted;
Acquiring the information to be submitted;
Reading this web page;
Submitting the information to us;
Exchanging data with receivers of your submission.
By following the procedures and tips below, you should be safe enough to send information without major risks:
Submit information using the Anonymous Web Browsing software Tor Browser, a piece of software designed to keep your identity protected while using the internet. It is easy to install, use, and needs no previous knowledge or experience;
Don’t submit information from the personal computer provided to you by your employer (consider using a spare one);
Save the Submission’s receipt in a secure location and destroy this information after you have ended your communications with the journalists;
Don’t keep a copy of the information you submitted;
Consider converting all the data that you are sending into standard PDF format.
To overall improve your digital security you should read the Security-in-a-Box project, which explains most of the risks and related countermeasures.

Before submitting any information you should consider what will happen “after” the information has been sent and when the news about the facts related to the info you submitted reaches public media attention.
Ask yourself the following questions to understand your real risk context:
Do people other than yourself have access to the information you are going to submit?
Are you really willing and ready to cope with an internal or external investigation about the submission?